Cards Collection
Browse all game cards by type
Bonus
Bonus Card
Advance by 2 spaces
Firewall
Defense System
Blocks Malware attacks but vulnerable to Backdoor exploits
Malware
Attack System
Exploits Backdoor vulnerabilities but stopped by Firewall
Backdoor
Stealth Entry
Bypasses Firewall protection but vulnerable to Malware
Firewall
Defense System
Blocks Malware attacks but vulnerable to Backdoor exploits
Malware
Attack System
Exploits Backdoor vulnerabilities but stopped by Firewall
Backdoor
Stealth Entry
Bypasses Firewall protection but vulnerable to Malware
Firewall
Defense System
Blocks Malware attacks but vulnerable to Backdoor exploits
Malware
Attack System
Exploits Backdoor vulnerabilities but stopped by Firewall
Backdoor
Stealth Entry
Bypasses Firewall protection but vulnerable to Malware
Malus
Malus Card
Choose someone to go backward by 2 spaces
OSINT Challenge #2
Security Breach Investigation
Discover how this PC was unlocked without permission

This PC has been unlocked by someone without permission. But how?
💡 Hints:
- • Look around the workspace area
- • Check for sticky notes or papers
- • Examine items near the computer
✅ Answer: Password is written on a post-it note
🔍 Investigation Tools:
- • Use reverse image search (Google Images, TinEye)
- • Check EXIF metadata for GPS coordinates
- • Analyze visible landmarks and text
- • Look for reflections and background details
OSINT Challenge #3
Resort Identification
Identify the resort from this island photo

This is a photo of a resort located on an island. What is the name of the resort?
💡 Hints:
- • Look for visible signage or branding
- • Use reverse image search
- • Check for architectural style clues
✅ Answer: Oan Resort
🔍 Investigation Tools:
- • Use reverse image search (Google Images, TinEye)
- • Check EXIF metadata for GPS coordinates
- • Analyze visible landmarks and text
- • Look for reflections and background details
OSINT Challenge #4
Document Dating
Find the publication date of this journal

Give the publication date of this journal.
💡 Hints:
- • Look for date stamps on the document
- • Check the header or footer area
- • Examine any visible metadata
✅ Answer: 2023/01/12 (January 12, 2023)
🔍 Investigation Tools:
- • Use reverse image search (Google Images, TinEye)
- • Check EXIF metadata for GPS coordinates
- • Analyze visible landmarks and text
- • Look for reflections and background details
OSINT Challenge #1
Workplace Investigation
Find the complete workplace information of this person
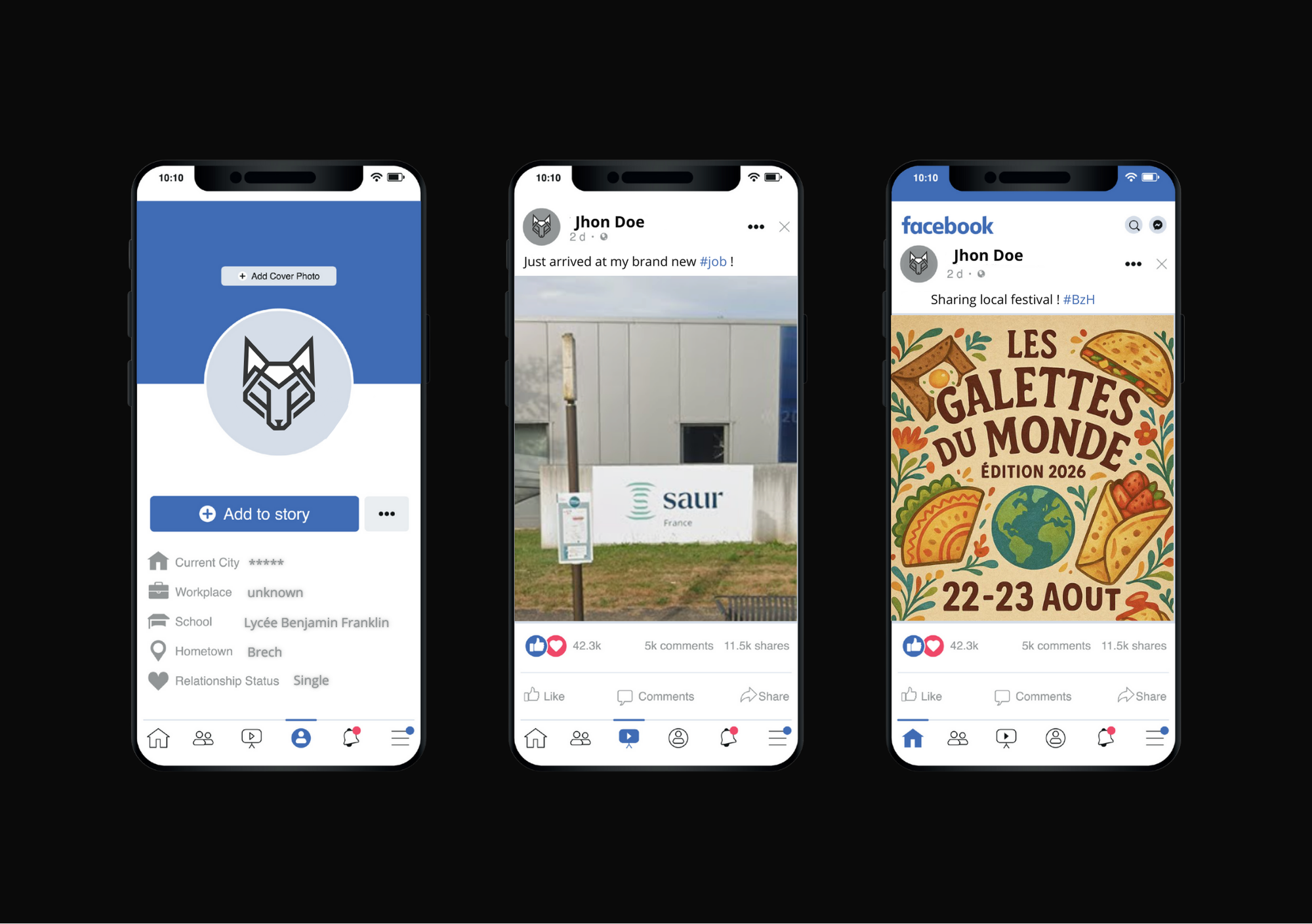
Give the Name, the City and the Street of the working place of this person.
💡 Hints:
- • Look for company logos or badges
- • Check for visible text on documents or uniforms
- • Search for street signs or location markers
✅ Answer: Job: SAUR, City: Auray, Street: Rue du Danemark
🔍 Investigation Tools:
- • Use reverse image search (Google Images, TinEye)
- • Check EXIF metadata for GPS coordinates
- • Analyze visible landmarks and text
- • Look for reflections and background details
OSINT Challenge #5
Artist Attribution
Identify the creator of this statue

Who is the creator of this statue?
💡 Hints:
- • Look for environment clues around the statue
- • Use reverse image search
- • Search for the sculpture style and location
✅ Answer: Jorge Vieira
🔍 Investigation Tools:
- • Use reverse image search (Google Images, TinEye)
- • Check EXIF metadata for GPS coordinates
- • Analyze visible landmarks and text
- • Look for reflections and background details
Post Office Package
Avoid the Trap
Is this email legitimate or phishing?
From:
noreply@postoffice-info.com
Subject:
Your package requires address confirmation
Message:
Click here to confirm your delivery address.
Link shown:
postoffice-verify.com/address
Is this email legitimate or phishing?
👉 Phishing
💡 Domain name slightly different from the real one.
Google Security Alert
Avoid the Trap
Is this email legitimate or phishing?
From:
security@google.com
Subject:
Unusual login detected
Message:
Hello, an unusual login has been detected on your account from Chicago. If this wasn't you, verify your activity through your account.
Link shown:
accounts.google.com
Real link:
accounts-google.com.security-check.com/
Is this email legitimate or phishing?
👉 Phishing
💡 Deceptive subdomain. Real link differs from displayed link.
Telecom Invoice
Avoid the Trap
Is this email legitimate or phishing?
From:
billing@telecom.com
Subject:
Your invoice for November
Message:
Attached PDF, file name: invoice_2025.pdf. No external links.
Attachment:
📎 invoice_2025.pdf
Is this email legitimate or phishing?
👉 Legitimate
💡 Telecom companies really send PDFs, no suspicious links.
Facebook Verification
Avoid the Trap
Is this email legitimate or phishing?
From:
security@facebookmail.com
Subject:
Account temporarily restricted
Message:
Your Facebook account has been temporarily restricted due to a report. Please verify your identity.
Link shown:
facebook.com/verify
Real link:
facebook.com.verify-support.fr
Is this email legitimate or phishing?
👉 Phishing
💡 Real trap: displayed link OK, actual link NOT OK.
Tax Authority Notice
Avoid the Trap
Is this email legitimate or phishing?
From:
contact@irs.gov
Subject:
Information about your latest notice
Message:
Redirect to the official irs.gov portal via secure link.
Link shown:
irs.gov
Is this email legitimate or phishing?
👉 Legitimate
💡 Official domain name + redirect to trusted site.
Amazon Security Team
Avoid the Trap
Is this email legitimate or phishing?
From:
account@amazon.com
Subject:
Suspicious activity detected
Message:
Suspicious activity has been detected on your Amazon account. To verify your orders, access your customer area.
Link shown:
amazon-checkorder.net
Is this email legitimate or phishing?
👉 Phishing
💡 Fake domain name.
PayPal Receipt
Avoid the Trap
Is this email legitimate or phishing?
From:
support@paypal.com
Subject:
Transaction verified: PayPal receipt
Message:
You often receive this type of email after a real purchase.
Is this email legitimate or phishing?
👉 Legitimate
💡 PayPal confirmations are very simple, often without alerts.
Instagram Warning
Avoid the Trap
Is this email legitimate or phishing?
From:
security@instagram.com
Subject:
Account will be deactivated soon
Message:
Hello, your Instagram account will soon be deactivated due to a violation of the rules. Call this number if you think this is an error.
Attachment:
📎 Phone: +1 555 123 4567
Is this email legitimate or phishing?
👉 Phishing
💡 Instagram never asks to call a phone number.
Online Store Order
Avoid the Trap
Is this email legitimate or phishing?
From:
shop@onlinestore.com
Subject:
Problem with your order
Message:
Link to onlinestore.com
Link shown:
onlinestore.com
Attachment:
📎 Order_STORE.pdf.exe
Is this email legitimate or phishing?
👉 Phishing
💡 Double extension (pdf.exe) = classic scam.
Bank Security Alert
Avoid the Trap
Is this email legitimate or phishing?
From:
alerts@yourbank.com
Subject:
Unusual payment detected
Message:
Your bank has detected an unusual payment. No action required if you recognize the transaction. Otherwise, visit your customer area. No link provided.
Is this email legitimate or phishing?
👉 Legitimate
💡 Banks often send this type of alert without clickable links.
Post Office Package
Avoid the Trap
Is this email legitimate or phishing?
From:
noreply@postoffice-info.com
Subject:
Your package requires address confirmation
Message:
Click here to confirm your delivery address.
Link shown:
postoffice-verify.com/address
Is this email legitimate or phishing?
👉 Phishing
💡 Domain name slightly different from the real one.
Google Security Alert
Avoid the Trap
Is this email legitimate or phishing?
From:
security@google.com
Subject:
Unusual login detected
Message:
Hello, an unusual login has been detected on your account from Chicago. If this wasn't you, verify your activity through your account.
Link shown:
accounts.google.com
Real link:
accounts-google.com.security-check.com/
Is this email legitimate or phishing?
👉 Phishing
💡 Deceptive subdomain. Real link differs from displayed link.
Telecom Invoice
Avoid the Trap
Is this email legitimate or phishing?
From:
billing@telecom.com
Subject:
Your invoice for November
Message:
Attached PDF, file name: invoice_2025.pdf. No external links.
Attachment:
📎 invoice_2025.pdf
Is this email legitimate or phishing?
👉 Legitimate
💡 Telecom companies really send PDFs, no suspicious links.
Facebook Verification
Avoid the Trap
Is this email legitimate or phishing?
From:
security@facebookmail.com
Subject:
Account temporarily restricted
Message:
Your Facebook account has been temporarily restricted due to a report. Please verify your identity.
Link shown:
facebook.com/verify
Real link:
facebook.com.verify-support.fr
Is this email legitimate or phishing?
👉 Phishing
💡 Real trap: displayed link OK, actual link NOT OK.
Tax Authority Notice
Avoid the Trap
Is this email legitimate or phishing?
From:
contact@irs.gov
Subject:
Information about your latest notice
Message:
Redirect to the official irs.gov portal via secure link.
Link shown:
irs.gov
Is this email legitimate or phishing?
👉 Legitimate
💡 Official domain name + redirect to trusted site.
Amazon Security Team
Avoid the Trap
Is this email legitimate or phishing?
From:
account@amazon.com
Subject:
Suspicious activity detected
Message:
Suspicious activity has been detected on your Amazon account. To verify your orders, access your customer area.
Link shown:
amazon-checkorder.net
Is this email legitimate or phishing?
👉 Phishing
💡 Fake domain name.
PayPal Receipt
Avoid the Trap
Is this email legitimate or phishing?
From:
support@paypal.com
Subject:
Transaction verified: PayPal receipt
Message:
You often receive this type of email after a real purchase.
Is this email legitimate or phishing?
👉 Legitimate
💡 PayPal confirmations are very simple, often without alerts.
Instagram Warning
Avoid the Trap
Is this email legitimate or phishing?
From:
security@instagram.com
Subject:
Account will be deactivated soon
Message:
Hello, your Instagram account will soon be deactivated due to a violation of the rules. Call this number if you think this is an error.
Attachment:
📎 Phone: +1 555 123 4567
Is this email legitimate or phishing?
👉 Phishing
💡 Instagram never asks to call a phone number.
Online Store Order
Avoid the Trap
Is this email legitimate or phishing?
From:
shop@onlinestore.com
Subject:
Problem with your order
Message:
Link to onlinestore.com
Link shown:
onlinestore.com
Attachment:
📎 Order_STORE.pdf.exe
Is this email legitimate or phishing?
👉 Phishing
💡 Double extension (pdf.exe) = classic scam.
Bank Security Alert
Avoid the Trap
Is this email legitimate or phishing?
From:
alerts@yourbank.com
Subject:
Unusual payment detected
Message:
Your bank has detected an unusual payment. No action required if you recognize the transaction. Otherwise, visit your customer area. No link provided.
Is this email legitimate or phishing?
👉 Legitimate
💡 Banks often send this type of alert without clickable links.
Telecom Invoice
Avoid the Trap - Easy
Is this email legitimate or phishing?
From:
billing@telecom.com
Subject:
Your invoice for November
Message:
Attached PDF, file name: invoice_2025.pdf. No external links.
Attachment:
📎 invoice_2025.pdf
Is this email legitimate or phishing?
👉 Legitimate
💡 Telecom companies really send PDFs, no suspicious links.
Amazon Security
Avoid the Trap - Easy
Is this email legitimate or phishing?
From:
account@amazon.com
Subject:
Suspicious activity detected
Message:
Suspicious activity has been detected on your Amazon account. To verify your orders, access your customer area.
Link shown:
amazon-checkorder.net
Is this email legitimate or phishing?
👉 Phishing
💡 Fake domain name.
PayPal Receipt
Avoid the Trap - Easy
Is this email legitimate or phishing?
From:
support@paypal.com
Subject:
Transaction verified: PayPal receipt
Message:
You often receive this type of email after a real purchase.
Is this email legitimate or phishing?
👉 Legitimate
💡 PayPal confirmations are very simple, often without alerts.
Post Office Package
Avoid the Trap - Medium
Is this email legitimate or phishing?
From:
noreply@postoffice-info.com
Subject:
Your package requires address confirmation
Message:
Click here to confirm your delivery address.
Link shown:
postoffice-verify.com/address
Is this email legitimate or phishing?
👉 Phishing
💡 Domain name slightly different from the real one.
Tax Authority
Avoid the Trap - Medium
Is this email legitimate or phishing?
From:
contact@irs.gov
Subject:
Information about your latest notice
Message:
Redirect to the official irs.gov portal via secure link.
Link shown:
irs.gov
Is this email legitimate or phishing?
👉 Legitimate
💡 Official domain name + redirect to trusted site.
Instagram Warning
Avoid the Trap - Medium
Is this email legitimate or phishing?
From:
security@instagram.com
Subject:
Account will be deactivated soon
Message:
Hello, your Instagram account will soon be deactivated due to a violation of the rules. Call this number if you think this is an error.
Attachment:
📎 Phone: +1 555 123 4567
Is this email legitimate or phishing?
👉 Phishing
💡 Instagram never asks to call a phone number.
Bank Alert
Avoid the Trap - Medium
Is this email legitimate or phishing?
From:
alerts@yourbank.com
Subject:
Unusual payment detected
Message:
Your bank has detected an unusual payment. No action required if you recognize the transaction. Otherwise, visit your customer area. No link provided.
Is this email legitimate or phishing?
👉 Legitimate
💡 Banks often send this type of alert without clickable links.
Google Security Alert
Avoid the Trap - Hard
Is this email legitimate or phishing?
From:
security@google.com
Subject:
Unusual login detected
Message:
Hello, an unusual login has been detected on your account from Chicago. If this wasn't you, verify your activity through your account.
Link shown:
accounts.google.com
Real link:
accounts-google.com.security-check.com/
Is this email legitimate or phishing?
👉 Phishing
💡 Deceptive subdomain. Real link differs from displayed link.
Facebook Verification
Avoid the Trap - Hard
Is this email legitimate or phishing?
From:
security@facebookmail.com
Subject:
Account temporarily restricted
Message:
Your Facebook account has been temporarily restricted due to a report. Please verify your identity.
Link shown:
facebook.com/verify
Real link:
facebook.com.verify-support.fr
Is this email legitimate or phishing?
👉 Phishing
💡 Real trap: displayed link OK, actual link NOT OK.
Online Store Order
Avoid the Trap - Hard
Is this email legitimate or phishing?
From:
shop@onlinestore.com
Subject:
Problem with your order
Message:
Link to onlinestore.com
Link shown:
onlinestore.com
Attachment:
📎 Order_STORE.pdf.exe
Is this email legitimate or phishing?
👉 Phishing
💡 Double extension (pdf.exe) = classic scam.
Password Security
Technical Quiz
Answer the cybersecurity question
Which password is the most secure?
- A. 123456
- B. azerty
- C. Soleil2025!
- D. motdepasse
Correct: C. Soleil2025!
HTTPS Security
Technical Quiz
Answer the cybersecurity question
What does the 🔒 icon in the address bar mean?
- A. The site is fast
- B. The site uses HTTPS
- C. The site is official
- D. The site has no ads
Correct: B. The site uses HTTPS
Email Fraud Detection
Technical Quiz
Answer the cybersecurity question
Which element can indicate a fraudulent email?
- A. An unknown address
- B. An elegant font
- C. A legitimate attachment
- D. A complete signature
Correct: A. An unknown address
Metadata in Files
Technical Quiz
Answer the cybersecurity question
What type of file can contain metadata revealing a location?
- A. .pdf
- B. .jpg
- C. .zip
- D. .csv
Correct: B. .jpg
Ransomware Definition
Technical Quiz
Answer the cybersecurity question
What is a ransomware?
- A. A virus that spams
- B. A virus that encrypts files
- C. A virus that shows ads
- D. A virus that steals passwords
Correct: B. A virus that encrypts files
Firewall Purpose
Technical Quiz
Answer the cybersecurity question
What is the purpose of a firewall?
- A. Delete viruses
- B. Block or allow network traffic
- C. Speed up internet connection
- D. Backup data
Correct: B. Block or allow network traffic
Phone Number Privacy
Technical Quiz
Answer the cybersecurity question
What is the main risk of posting your phone number publicly?
- A. Battery drain
- B. Spam + targeted attacks
- C. Account deletion
- D. Carrier blocking
Correct: B. Spam + targeted attacks
Wi-Fi Encryption
Technical Quiz
Answer the cybersecurity question
Which protocol encrypts communications on a secure Wi-Fi network?
- A. WEP
- B. WPA2
- C. FTP
- D. ARP
Correct: B. WPA2
SQL Injection
Technical Quiz
Answer the cybersecurity question
What type of attack exploits a vulnerability in web forms?
- A. DDoS
- B. Man-in-the-middle
- C. SQL Injection
- D. Sniffing
Correct: C. SQL Injection
Password Cracking
Technical Quiz
Answer the cybersecurity question
Which method tests password strength without knowing it?
- A. Social engineering
- B. Heuristic analysis
- C. Bruteforce
- D. Network reconnaissance
Correct: C. Bruteforce
RIWLFEAL
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
RIWLFEAL
💡 Hint: Network security device
Answer: FIREWALL
NYRPCTIEON
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NYRPCTIEON
💡 Hint: Data protection method
Answer: ENCRYPTION
SWASROPD
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
SWASROPD
💡 Hint: Authentication credential
Answer: PASSWORD
HACEKR
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
HACEKR
💡 Hint: Cyber intruder
Answer: HACKER
MLAAREW
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
MLAAREW
💡 Hint: Malicious software
Answer: MALWARE
GIHSNIHP
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
GIHSNIHP
💡 Hint: Email scam technique
Answer: PHISHING
KAOBRCDO
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
KAOBRCDO
💡 Hint: Hidden access point
Answer: BACKDOOR
UISVR
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
UISVR
💡 Hint: Self-replicating malware
Answer: VIRUS
NOARSWEM
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NOARSWEM
💡 Hint: Encrypts files for money
Answer: RANSOMWARE
VPN
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
VPN
💡 Hint: Virtual Private Network (already unscrambled - explain what it stands for!)
Answer: VPN
RIWLFEAL
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
RIWLFEAL
💡 Hint: Network security device
Answer: FIREWALL
NYRPCTIEON
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NYRPCTIEON
💡 Hint: Data protection method
Answer: ENCRYPTION
SWASROPD
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
SWASROPD
💡 Hint: Authentication credential
Answer: PASSWORD
HACEKR
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
HACEKR
💡 Hint: Cyber intruder
Answer: HACKER
MLAAREW
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
MLAAREW
💡 Hint: Malicious software
Answer: MALWARE
GIHSNIHP
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
GIHSNIHP
💡 Hint: Email scam technique
Answer: PHISHING
KAOBRCDO
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
KAOBRCDO
💡 Hint: Hidden access point
Answer: BACKDOOR
UISVR
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
UISVR
💡 Hint: Self-replicating malware
Answer: VIRUS
NOARSWEM
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NOARSWEM
💡 Hint: Encrypts files for money
Answer: RANSOMWARE
VPN
Group Challenge
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
VPN
💡 Hint: Virtual Private Network (already unscrambled - explain what it stands for!)
Answer: VPN
SWASROPD
Group Challenge - Easy
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
SWASROPD
💡 Hint: Authentication credential
Answer: PASSWORD
HACEKR
Group Challenge - Easy
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
HACEKR
💡 Hint: Cyber intruder
Answer: HACKER
UISVR
Group Challenge - Easy
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
UISVR
💡 Hint: Self-replicating malware
Answer: VIRUS
RIWLFEAL
Group Challenge - Medium
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
RIWLFEAL
💡 Hint: Network security device
Answer: FIREWALL
MLAAREW
Group Challenge - Medium
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
MLAAREW
💡 Hint: Malicious software
Answer: MALWARE
VPN
Group Challenge - Medium
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
VPN
💡 Hint: Virtual Private Network (already unscrambled - explain what it stands for!)
Answer: VPN
NYRPCTIEON
Group Challenge - Hard
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NYRPCTIEON
💡 Hint: Data protection method
Answer: ENCRYPTION
GIHSNIHP
Group Challenge - Hard
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
GIHSNIHP
💡 Hint: Email scam technique
Answer: PHISHING
KAOBRCDO
Group Challenge - Hard
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
KAOBRCDO
💡 Hint: Hidden access point
Answer: BACKDOOR
NOARSWEM
Group Challenge - Hard
First to unscramble this cyber term moves up, last player moves down
Scrambled Word:
NOARSWEM
💡 Hint: Encrypts files for money
Answer: RANSOMWARE
Expert Phishing Detection
Special Challenge - Expert
Advanced phishing detection - analyze carefully!
From:
noreply-update@microsoft.com
Subject:
Mandatory update of terms of service
Real link:
https://account.microsoft.com.security-policy.net
❓ Is this legitimate or dangerous?
🔥 Dangerous
💡 Main domain = security-policy.net, not microsoft.com. The subdomain trick makes it look legitimate.
Password Strength Expert
Special Challenge - Expert
Which password is truly the strongest?
Which is really the strongest password?
- A. &T4p9Lm!2
- B. GreenButterflyHitsAWallIn2025
- C. N!k0lA5-R00
- D. %zF3-@Lp
🔥 N/A
💡 A long passphrase beats a short complex password. Length > complexity for security.
Social Engineering Attack
Special Challenge - Expert
Real enterprise threat scenario
A "technician" calls you: "We need to reset your MFA due to an issue. I'll send you a code, read it to me to validate."
📋 The call seems internal (company number displayed)
❓ Is this legitimate?
🔥 No - Attack
💡 This is reverse-MFA (very common attack). Real IT never asks you to read MFA codes over phone.
Mixed Content Security
Special Challenge - Expert
Technical web security analysis
A website uses HTTPS, but loads an external script via HTTP.
📋 Main page: https:// | External script: http://
❓ Is this secure?
🔥 No - Insecure
💡 Unencrypted script allows Man-in-the-Middle attacks. One HTTP resource compromises entire HTTPS page.
Evil Twin WiFi
Special Challenge - Expert
Network security threat detection
Employee connects to "Company-Secure" (WPA2, normally no captive portal).
📋 Phone suddenly opens a login page like a captive portal
❓ Bug or security risk?
🔥 Security Risk
💡 Probable rogue access point (Evil Twin attack). Real network doesn't use captive portal.
Modern Malware Behavior
Special Challenge - Expert
Identify advanced malware characteristics
Which behavior indicates modern stealthy malware?
- A. PC overheating
- B. Screen flickering
- C. No visible symptoms
- D. Pop-ups appearing
🔥 N/A
💡 Serious malware shows NO symptoms. Obvious signs = amateur malware or adware.
Technical Email Phishing
Special Challenge - Expert
Very tricky phishing detection
From:
support@paypal.com
Subject:
Security verification required
Link displayed:
https://paypal.com/security
Real link:
https://paypal.com.security-check.info
❓ Is this legitimate?
🔥 No - Phishing
💡 Master domain = security-check.info. The real domain comes AFTER the last dot before the first slash.
MFA Authentication Logic
Special Challenge - Expert
Advanced authentication reasoning
A company replaces passwords with a 6-digit PIN + MFA application.
📋 Old: Long password only | New: Short PIN + MFA app
❓ Does this reduce security?
🔥 No - Still Secure
💡 The PIN becomes secondary: MFA secures the access. 2FA with weak password > password-only with strong password.
RDP Network Exposure
Special Challenge - Expert
Server security assessment
A Windows server exposes port 3389 (RDP) on the Internet.
📋 Security measures: Long password, MFA enabled, Active firewall
❓ Is this sufficient?
🔥 No - Insufficient
💡 Exposed RDP = massive automated attacks. Must use VPN + IP filtering. Never expose RDP directly to Internet.
SSL Certificate Trust
Special Challenge - Expert
Expert certificate analysis
Banking site in HTTPS with valid certificate.
📋 Padlock OK, Valid certificate, Issuer: Let's Encrypt, No browser alert
❓ Is this sufficient proof the site is authentic?
🔥 No - Not Sufficient
💡 A valid certificate = encryption, NOT identity. Anyone can get free Let's Encrypt cert for phishing sites.
Expert Phishing Detection
Special Challenge - Expert
Advanced phishing detection - analyze carefully!
From:
noreply-update@microsoft.com
Subject:
Mandatory update of terms of service
Real link:
https://account.microsoft.com.security-policy.net
❓ Is this legitimate or dangerous?
🔥 Dangerous
💡 Main domain = security-policy.net, not microsoft.com. The subdomain trick makes it look legitimate.
Password Strength Expert
Special Challenge - Expert
Which password is truly the strongest?
Which is really the strongest password?
- A. &T4p9Lm!2
- B. GreenButterflyHitsAWallIn2025
- C. N!k0lA5-R00
- D. %zF3-@Lp
🔥 N/A
💡 A long passphrase beats a short complex password. Length > complexity for security.
Social Engineering Attack
Special Challenge - Expert
Real enterprise threat scenario
A "technician" calls you: "We need to reset your MFA due to an issue. I'll send you a code, read it to me to validate."
📋 The call seems internal (company number displayed)
❓ Is this legitimate?
🔥 No - Attack
💡 This is reverse-MFA (very common attack). Real IT never asks you to read MFA codes over phone.
Mixed Content Security
Special Challenge - Expert
Technical web security analysis
A website uses HTTPS, but loads an external script via HTTP.
📋 Main page: https:// | External script: http://
❓ Is this secure?
🔥 No - Insecure
💡 Unencrypted script allows Man-in-the-Middle attacks. One HTTP resource compromises entire HTTPS page.
Evil Twin WiFi
Special Challenge - Expert
Network security threat detection
Employee connects to "Company-Secure" (WPA2, normally no captive portal).
📋 Phone suddenly opens a login page like a captive portal
❓ Bug or security risk?
🔥 Security Risk
💡 Probable rogue access point (Evil Twin attack). Real network doesn't use captive portal.
Modern Malware Behavior
Special Challenge - Expert
Identify advanced malware characteristics
Which behavior indicates modern stealthy malware?
- A. PC overheating
- B. Screen flickering
- C. No visible symptoms
- D. Pop-ups appearing
🔥 N/A
💡 Serious malware shows NO symptoms. Obvious signs = amateur malware or adware.
Technical Email Phishing
Special Challenge - Expert
Very tricky phishing detection
From:
support@paypal.com
Subject:
Security verification required
Link displayed:
https://paypal.com/security
Real link:
https://paypal.com.security-check.info
❓ Is this legitimate?
🔥 No - Phishing
💡 Master domain = security-check.info. The real domain comes AFTER the last dot before the first slash.
MFA Authentication Logic
Special Challenge - Expert
Advanced authentication reasoning
A company replaces passwords with a 6-digit PIN + MFA application.
📋 Old: Long password only | New: Short PIN + MFA app
❓ Does this reduce security?
🔥 No - Still Secure
💡 The PIN becomes secondary: MFA secures the access. 2FA with weak password > password-only with strong password.
RDP Network Exposure
Special Challenge - Expert
Server security assessment
A Windows server exposes port 3389 (RDP) on the Internet.
📋 Security measures: Long password, MFA enabled, Active firewall
❓ Is this sufficient?
🔥 No - Insufficient
💡 Exposed RDP = massive automated attacks. Must use VPN + IP filtering. Never expose RDP directly to Internet.
SSL Certificate Trust
Special Challenge - Expert
Expert certificate analysis
Banking site in HTTPS with valid certificate.
📋 Padlock OK, Valid certificate, Issuer: Let's Encrypt, No browser alert
❓ Is this sufficient proof the site is authentic?
🔥 No - Not Sufficient
💡 A valid certificate = encryption, NOT identity. Anyone can get free Let's Encrypt cert for phishing sites.
Expert Phishing Detection
Special Challenge - Expert
Advanced phishing detection - analyze carefully!
From:
noreply-update@microsoft.com
Subject:
Mandatory update of terms of service
Real link:
https://account.microsoft.com.security-policy.net
❓ Is this legitimate or dangerous?
🔥 Dangerous
💡 Main domain = security-policy.net, not microsoft.com. The subdomain trick makes it look legitimate.
Password Strength Expert
Special Challenge - Expert
Which password is truly the strongest?
Which is really the strongest password?
- A. &T4p9Lm!2
- B. GreenButterflyHitsAWallIn2025
- C. N!k0lA5-R00
- D. %zF3-@Lp
🔥 N/A
💡 A long passphrase beats a short complex password. Length > complexity for security.
Social Engineering Attack
Special Challenge - Expert
Real enterprise threat scenario
A "technician" calls you: "We need to reset your MFA due to an issue. I'll send you a code, read it to me to validate."
📋 The call seems internal (company number displayed)
❓ Is this legitimate?
🔥 No - Attack
💡 This is reverse-MFA (very common attack). Real IT never asks you to read MFA codes over phone.
Mixed Content Security
Special Challenge - Expert
Technical web security analysis
A website uses HTTPS, but loads an external script via HTTP.
📋 Main page: https:// | External script: http://
❓ Is this secure?
🔥 No - Insecure
💡 Unencrypted script allows Man-in-the-Middle attacks. One HTTP resource compromises entire HTTPS page.
Evil Twin WiFi
Special Challenge - Expert
Network security threat detection
Employee connects to "Company-Secure" (WPA2, normally no captive portal).
📋 Phone suddenly opens a login page like a captive portal
❓ Bug or security risk?
🔥 Security Risk
💡 Probable rogue access point (Evil Twin attack). Real network doesn't use captive portal.
Modern Malware Behavior
Special Challenge - Expert
Identify advanced malware characteristics
Which behavior indicates modern stealthy malware?
- A. PC overheating
- B. Screen flickering
- C. No visible symptoms
- D. Pop-ups appearing
🔥 N/A
💡 Serious malware shows NO symptoms. Obvious signs = amateur malware or adware.
Technical Email Phishing
Special Challenge - Expert
Very tricky phishing detection
From:
support@paypal.com
Subject:
Security verification required
Link displayed:
https://paypal.com/security
Real link:
https://paypal.com.security-check.info
❓ Is this legitimate?
🔥 No - Phishing
💡 Master domain = security-check.info. The real domain comes AFTER the last dot before the first slash.
MFA Authentication Logic
Special Challenge - Expert
Advanced authentication reasoning
A company replaces passwords with a 6-digit PIN + MFA application.
📋 Old: Long password only | New: Short PIN + MFA app
❓ Does this reduce security?
🔥 No - Still Secure
💡 The PIN becomes secondary: MFA secures the access. 2FA with weak password > password-only with strong password.
RDP Network Exposure
Special Challenge - Expert
Server security assessment
A Windows server exposes port 3389 (RDP) on the Internet.
📋 Security measures: Long password, MFA enabled, Active firewall
❓ Is this sufficient?
🔥 No - Insufficient
💡 Exposed RDP = massive automated attacks. Must use VPN + IP filtering. Never expose RDP directly to Internet.
SSL Certificate Trust
Special Challenge - Expert
Expert certificate analysis
Banking site in HTTPS with valid certificate.
📋 Padlock OK, Valid certificate, Issuer: Let's Encrypt, No browser alert
❓ Is this sufficient proof the site is authentic?
🔥 No - Not Sufficient
💡 A valid certificate = encryption, NOT identity. Anyone can get free Let's Encrypt cert for phishing sites.